AzureAD Passwordless Sign in - Part 1
Microsoft is currently on a path to switch services to Passwordless logins, meaning we will at some point no longer require a password. This does not mean accounts will not be protected; accounts will be using tokens, Multi-Factor, authenticator apps to perform authentication.
- The Microsoft strategy is base on 4 steps;
- Develop password replacement offering
- Reduce the user-visible password surface area
- Transition into password-less deployment
- Eliminate password from identity directory
Right now, we still see the continued development of the replacement for passwords and the reduction of locations where we need to enter password. So we are some time away from removing passwords.
The Microsoft strategy is documented here: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/passwordless-strategy
AzureAD has options to start using Passwordless logins, so here I will go over some options.
AzureAD Passwordless login uses Microsoft AzureAD Multi-factor authentication(MFA) to log in. MFA uses “Something you have” and “Something you are or know” to provide the Passwordless login. We have two options for Passwordless, Microsoft Authenticator App or FIDO2 security key. These two options, combined with Windows Hello provides Passwordless login.
Microsoft Authenticator App once enabled, will prompt the user to confirm a number on the login page with a number on the App. If correct the user is authenticated.

FIDO2 Security Keys uses Fast Identity Online (FIDO) standard for Passwordless authentication; they are usually an external physical key or built into a platform key which is built in the device.
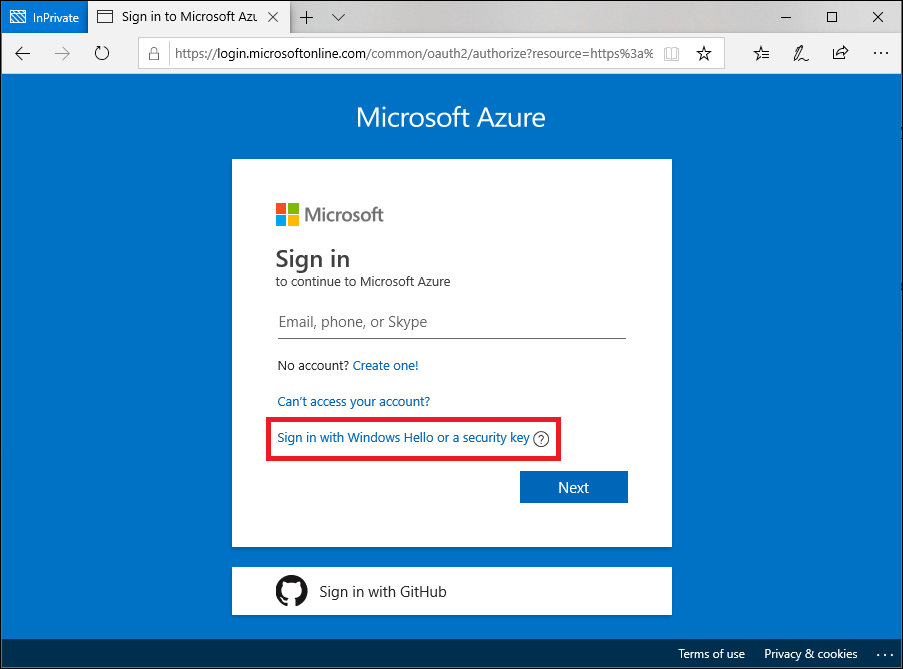
AzureAD for Passwordless login set up with Microsoft Authenticator App.
I assume at this point; you have AzureAD MFA setup. This is a requirement and should be configured first.
To enable Passwordless phone sign-in,
- Open Azure Portal and navigate to Azure Active Directory.
- Scroll down to the Authentication Methods policy (Preview) section.
- In the Microsoft Authenticator passwordless sign-in, select Enable and All users, you can just enable a group if you wish.
- Click Save.
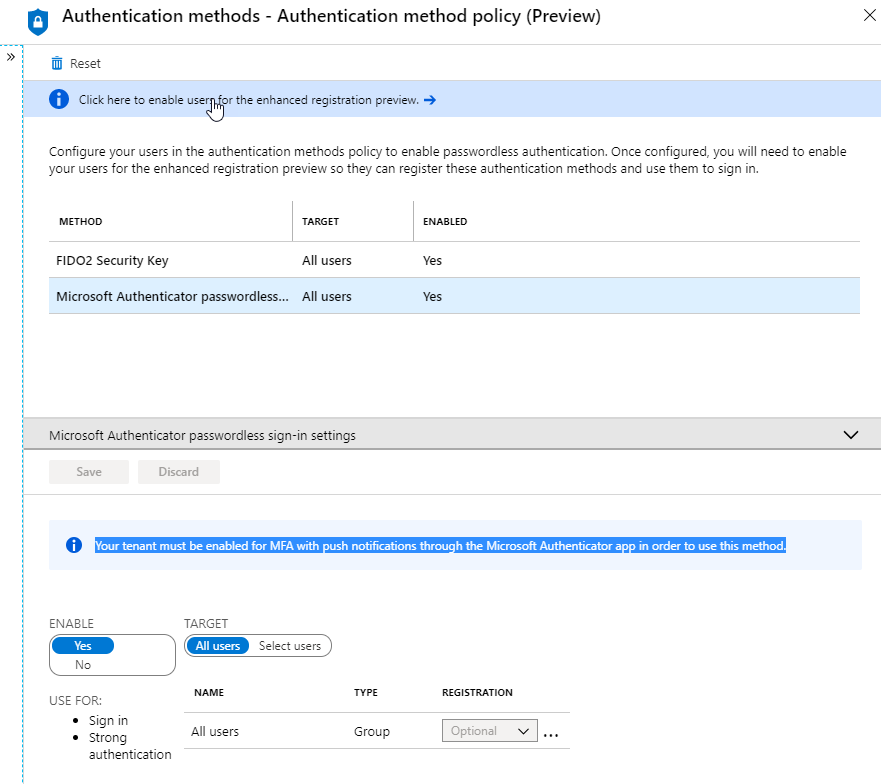
User registration and Microsoft Authenticator App management.
Users can self manage their MFA settings via the security portal. The first stage is to make sure you have the App installed.
- Browse to https://aka.ms/mysecurityinfo
- Add an authenticator app by clicking Add method, choosing Authenticator app, and clicking Add
- Follow the instructions to install and configure the Microsoft Authenticator app on your device
- Click Done to complete Authenticator MFA app setup flow.
Once the App has been installed on your device;
- Open the Microsoft Authenticator app on your device
- Select the account you wish to enable
- Tap on the drop-down arrow and select Enable phone sign-in
- Follow the prompts on the app to complete the registration
At this point, the user now has an option for passwordless login. The feature is in preview, so some services will not force the passwordless and may switch back to standard methods.
There is a known issue with AD FS based hybrid Azure AD; it does not fully support the passwordless login. AD FS will switch back to sending a notification to the user if they attempt a passwordless login.
In the next section, we will look at enabling the FIDO keys.
Posts in Series:
AzureAD Passwordless Sign in with FIDO - Part 1
