AzureAD Passwordless Sign in, forcing Windows 10 to login with FIDO only - Part 3

FIDO keys provide you with a hardware-based authentication device. The keys can be used on a number of different sites as well. I use the keys to protect my AzureAD login, GitHub and a few other places as well. In this section I will go over the configuration for locking down a Windows 10 device. I have already gone over the process to enable AzureAD in part 1 and 2.
AzureAD Passwordless Sign in with FIDO - Part 1
AzureAD Passwordless Sign in with FIDO - Part 2
In this post, I will give over how to enable secure login to Windows 10 using Intune. I assume that AzureAD and users are all set up.
To enabling security keys for sign-in in Intune
- Browse to https://portal.azure.com
- Select Microsoft Intune, then Device enrollment
- Select Windows enrollment, then Windows Hello for Business
- Enable both Allow phone sign-in and Use security key for sign-in. This will allow Windows Hello to perform logins via the phone or security key.
Next, we need to enable the devices to support FIDO keys.
- Browse to https://portal.azure.com
- Select Microsoft Intune, then Device configuration
- Select Profiles, then Create a profile
- Enter the following details into the profile
Name: Security Key for Windows Sign-In
Description: Enable FIDO security key for device sign-in
Platform: Windows 10 and later
Profile: Custom
Setting:
Name: Turn on FIDO Security Key for Windows Sign-In
Description: Turn on FIDO Security Key for Windows Sign-In
OMA-URI: ./Device/Vendor/MSFT/PassportForWork/SecurityKey/UseSecurityKeyForSignin
Data type: Integer
Value: 1
Assignment: Assign to All Users and All Devices
Now once the configuration has been pushed out by Intune, the devices will have a new login option.
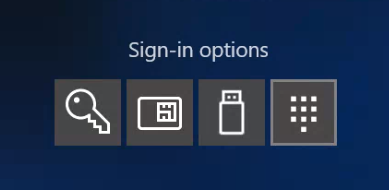
To use the key, insert it into the USB port and click on the USB icon on the login screen. You will be prompt to enter the FIDO security key pin and touch the key.
Removing Sign-in Options from users
The next stage is to lock down the Windows clients so they can only login with a FIDO key and nothing else. This can be done by blocking credential providers. All providers have the option to enable or disable. This can be done via GPO if you know the GUID for each provider.
Here is the list of the primary providers:
1b283861-754f-4022-ad47-a5eaaa618894 - “Smartcard Reader Selection Provider”
2135f72a-90b5-4ed3-a7f1-8bb705ac276a - “PicturePasswordLogonProvider”
25CBB996-92ED-457e-B28C-4774084BD562 - “GenericProvider”
27FBDB57-B613-4AF2-9D7E-4FA7A66C21AD - “TrustedSignal Credential Provider”
2D8B3101-E025-480D-917C-835522C7F628 - “FIDO Credential Provider”
3dd6bec0-8193-4ffe-ae25-e08e39ea4063 - “NPProvider”
60b78e88-ead8-445c-9cfd-0b87f74ea6cd - “PasswordProvider”
8AF662BF-65A0-4D0A-A540-A338A999D36F - “FaceCredentialProvider”
8FD7E19C-3BF7-489B-A72C-846AB3678C96 - “Smartcard Credential Provider”
94596c7e-3744-41ce-893e-bbf09122f76a - “Smartcard Pin Provider”
A910D941-9DA9-4656-8933-AA1EAE01F76E - “Remote NGC Credential Provider”
BEC09223-B018-416D-A0AC-523971B639F5 - “WinBio Credential Provider”
C885AA15-1764-4293-B82A-0586ADD46B35 - “IrisCredentialProvider”
cb82ea12-9f71-446d-89e1-8d0924e1256e - “PINLogonProvider”
D6886603-9D2F-4EB2-B667-1971041FA96B - “NGC Credential Provider”
F8A0B131-5F68-486c-8040-7E8FC3C85BB6 - “WLIDCredentialProvider”
F8A1793B-7873-4046-B2A7-1F318747F427 - “FIDO Credential Provider”
You can use Group Policy to deploy an administrative template policy setting to the computer. This policy setting is found under Computer Configuration > Policies > Administrative Templates > Logon > Exclude credential provider
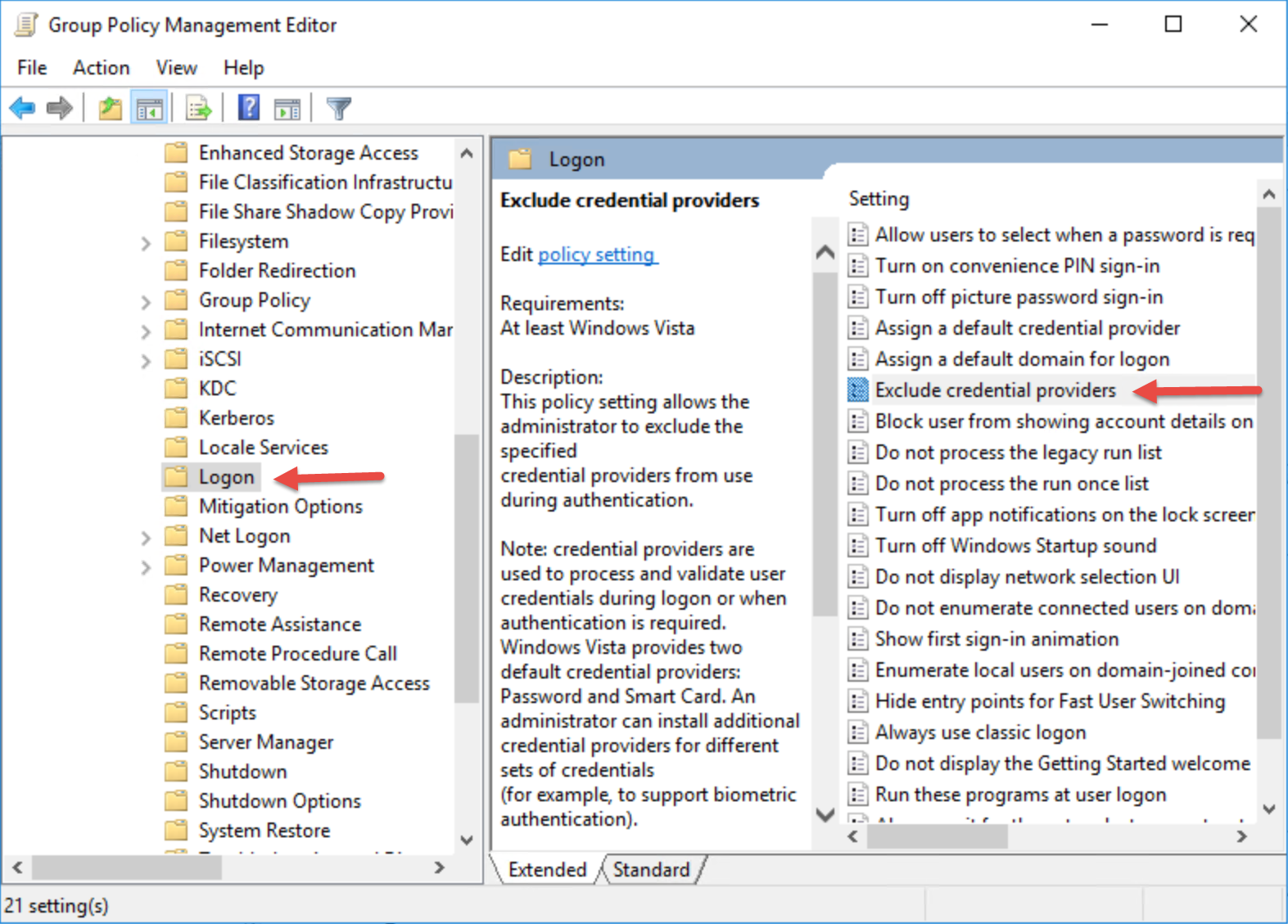
As I said, we would focus on the Intune. Intune does not have the same option as a GPO. So for a cloud base deployment, we will need to use OMA settings or PowerShell. The following process will use PowerShell to make changes to the registry.
The credential providers are located here:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers
Each of the providers is linked via their GUID. Under each key, we need to add the DWORD key, “Disabled” and set it to 1 for disabled or 0 for enabled. For example to disable the Password Login,
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{60b78e88-ead8-445c-9cfd-0b87f74ea6cd}]
@=“PasswordProvider”
“Disabled”=“1”
In Intune, we can deploy these via PowerShell scripts. I have created a script that will allow you to enable or disable the login providers. It is currently set to disable Password and Local Pin.
# Disabled flag, used to check and enable or disable login provider.
# 1 = Disabled credential provider
# 0 = Enabled credential provider
$DisbaleFlag = "1"
# Registry keys for removing Password and Pin login.
$registryKeys =
@(
[pscustomobject]@{Name="PasswordProvider";Location="HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{60b78e88-ead8-445c-9cfd-0b87f74ea6cd}";Key="Disabled";Value="1"},
# [pscustomobject]@{Name="PINLogonProvider";Location="HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{cb82ea12-9f71-446d-89e1-8d0924e1256e}";Key="Disabled";Value="1"},
# [pscustomobject]@{Name="IrisCredentialProvider";Location="HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{C885AA15-1764-4293-B82A-0586ADD46B35}";Key="Disabled";Value="1"},
[pscustomobject]@{Name="NGC Credential Provider";Location="HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{D6886603-9D2F-4EB2-B667-1971041FA96B}";Key="Disabled";Value="1"}
)
Write-output "Starting check for providers." | Out-File $env:temp\credprovlog.txt
Write-output "" | Out-File $env:temp\credprovlog.txt
foreach ($registrykey in $registryKeys)
{
Write-output "Checking Credential Provider $($registrykey.Name)" | Out-File $env:temp\credprovlog.txt
Write-output "----------------------------------------------------------------------------------------" | Out-File $env:temp\credprovlog.txt
$value = (Get-ItemProperty $registrykey.Location -ErrorAction SilentlyContinue).$($registrykey.Key)
If ($value -eq "1")
{
Write-output " $($registrykey.Name) Credential Provider exists, currently set to disabled login." | Out-File $env:temp\credprovlog.txt
If ($DisbaleFlag -eq "0")
{
Write-output " Enabling Credential Provider $($registrykey.Name)" | Out-File $env:temp\credprovlog.txt
try
{
New-ItemProperty -Path $registrykey.Location -Name $($registrykey.Key) -Value "0" -Force -ErrorAction SilentlyContinue | Out-Null
}
catch
{
Write-output " Error - Enabling Credential Provider $($registrykey.Name)" | Out-File $env:temp\credprovlog.txt
}
}
}
Else
{
Write-output " $($registrykey.Name) Credential Provider exists does not exist or is set to enabled"
If ($DisbaleFlag -eq "1")
{
Write-output " Disabling Credential Provider $($registrykey.Name)" | Out-File $env:temp\credprovlog.txt
try
{
New-ItemProperty -Path $registrykey.Location -Name $($registrykey.Key) -Value "1" -Force -ErrorAction SilentlyContinue | Out-Null
}
catch
{
Write-output " Error - Disabling Credential Provider $($registrykey.Name)" | Out-File $env:temp\credprovlog.txt
}
}
}
Write-output "----------------------------------------------------------------------------------------" | Out-File $env:temp\credprovlog.txt
}
Write-output "Completed." | Out-File $env:temp\credprovlog.txt
The following steps are used to deploy the script to devices. I have set up an AzureAD group and add the workstations I want to secure to that group. This allows me to secure specific workstations and not break other users logins.
To publish the PowerShell script;
- Browse to https://portal.azure.com
- Select Microsoft Intune, then Device Configuration
- Select PowerShell scripts, then Add
- Enter a name and descriptions for the script; I.e. secure-windows_login then click next
- Upload the script and select the following options and click next
Run this script using the logged on credentials, No Enforce script signature check, No Run the script in 64 bit PowerShell Host, Yes
- On the assignments page, select the security group which holds your devices which you want to lockdown.
Once Intune as pushed the script out to the devices, the user’s login screen will change. Before the script the user will have the following view;
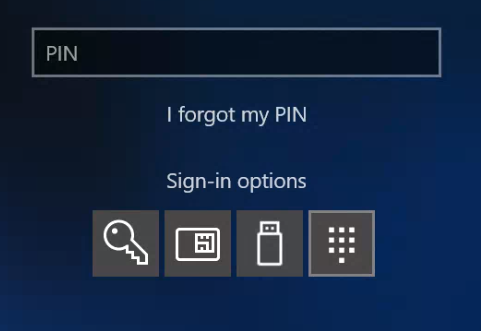
Post the script the user will now only see the following;
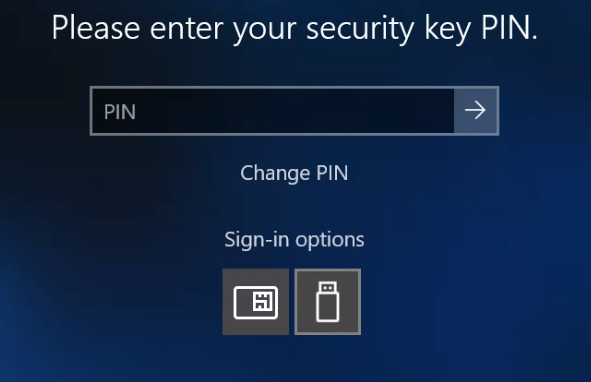
The device will now only accept sign in via the secure key. This can be changed by deploying the script and changing the flag to enable. If the user lost their key, they can re-add a new key via AzureAD and log back in.
Posts in Series:
AzureAD Passwordless Sign in with FIDO - Part 1
