University Project - OSINT and Cloud Services discovery tools
OSINT and Cloud Services Discovery Tools
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats and vulnerabilities is paramount. As organizations increasingly migrate their operations to the cloud, the need to secure cloud services and infrastructure has become more critical than ever. In this blog post, we delve into the world of Open-Source Intelligence (OSINT) and Cloud Services discovery tools, shedding light on a powerful code designed to uncover potential attack vectors within Azure/Microsoft 365 tenant cloud services.
In today’s digital age, attackers continually seek opportunities to exploit misconfigurations and weaknesses in cloud environments. Whether it’s on-premises systems or cloud services, systems administrators face the daunting challenge of securing their infrastructure effectively. This post explores a proactive approach to identifying potential attack surfaces within cloud services, drawing parallels with traditional network scanning techniques, such as NMAP and ENUM4LINUX, and introducing the concept of OSINT scans using a specialized tool called SHERLOCK.
Our journey into the realm of cloud service discovery will focus on a tool meticulously crafted to harness the power of Open-Source Intelligence, gathering data from DNS servers and leveraging Microsoft Azure AD PowerShell for authenticated information retrieval. What’s more, this invaluable tool is openly available to the cybersecurity community, as it has been published on GitHub. This means that security analysts and professionals worldwide can access, utilize, and contribute to its development.
This tool isn’t designed for malicious purposes but, rather, serves as a valuable resource for security analysts. It empowers them to gain a deeper understanding of their organization’s cloud service configurations and identify potential endpoints susceptible to cyber threats. Join us as we embark on a comprehensive exploration of OSINT and Cloud Services discovery tools, aiming to enhance your knowledge and bolster your organization’s security posture while highlighting the collaborative spirit of the cybersecurity community on GitHub.
The tool captures information using Open-Source Intelligence to collect from DNS servers and Microsoft Azure AD PowerShell for authenticated information. It was created for security analysts to understand what is configured and the possible endpoint of an attack.
The scripts are broken into three main files.
- Setup-PowerShellModule.ps1 -> Used to configure PowerShell Modules
- Find-AzureADOSint.ps1 -> Used to capture public information (OSINT)
- Find-AzureADInformation.ps1 -> Used to capture authenticated information (Enumeration)
The tool has been developed in Microsoft PowerShell version 5. It used Microsoft AzureAD PowerShell module version 2.0.2. The DNS queries are performed over HTTP using Google and Cloudflare’s DNS over HTTP services.
Configuration and Execution
The tool uses Microsoft PowerShell and will require additional PowerShell modules.
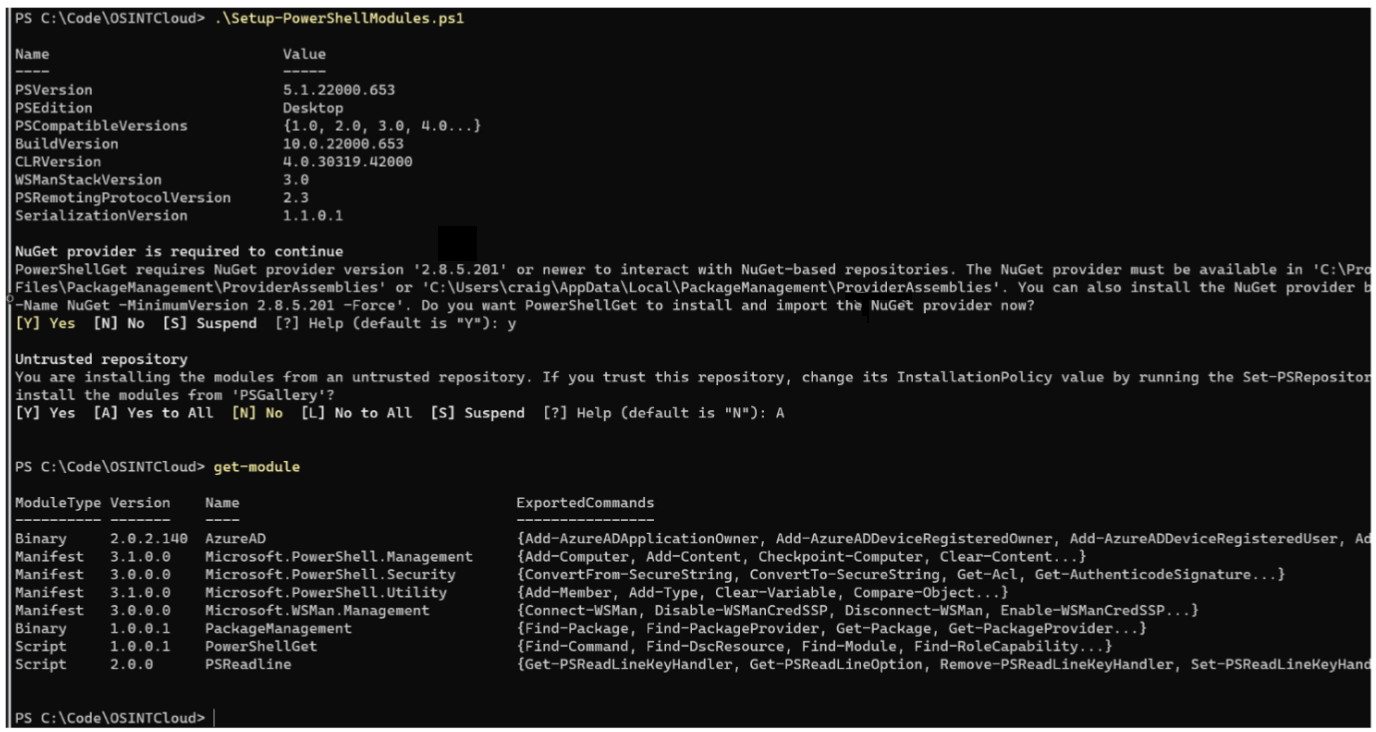
The script file “Setup-PowerShellModule.ps1” will install the required modules. To execute, run the following commands.
- Download the code from https://github.com/CraigWilsonOZ/OSINTCloud using git clone or copy. Make sure the files are unblocked
- Open a Windows Terminal PowerShell as Administrator
- Confirm PowerShell version is 5.1.x; type the following
$PSversionTable
- Type the following command to execute the install
Setup-PowerShellModule.ps1
- Accept the NuGet provider and Untrusted Repository prompts to install the modules
“Find-AzureADOSint.ps1” uses PowerShell to call DNS over HTTP. The script uses the following options.
Option Description
-domainname # The domain name that will be scanned
-usegoogledns # Flag to use Google DNS if true and CloudFlare if false
-wordlist # Use to supply a wordlist; if not supplied, the include wordlist.txt file is used.
To run the script, type the following commands.
- Open a Windows Terminal PowerShell as Administrator (Microsoft, 2022)
- Navigate to the downloaded code
- Type the following command, replacing “domain.com” with your “domain”
.\find-AzureADOSINT.ps1 -DomainName domain.com -Wordlist .\wordlist.txt -UseGoogleDNS $true
The code will scan DNS for available records, then brute force checks using “wordlist” for the following Azure Services:
- Azure API Manager (Publishing API endpoint to the Internet)
- Azure Front Door (Web Application Firewall and Load balancer publishing sites)
- Azure Storage Accounts (Storage blog account publishing SMB/CIFS Shares and data)
- AzureAD App Proxy (Publishing internal websites to the Internet)
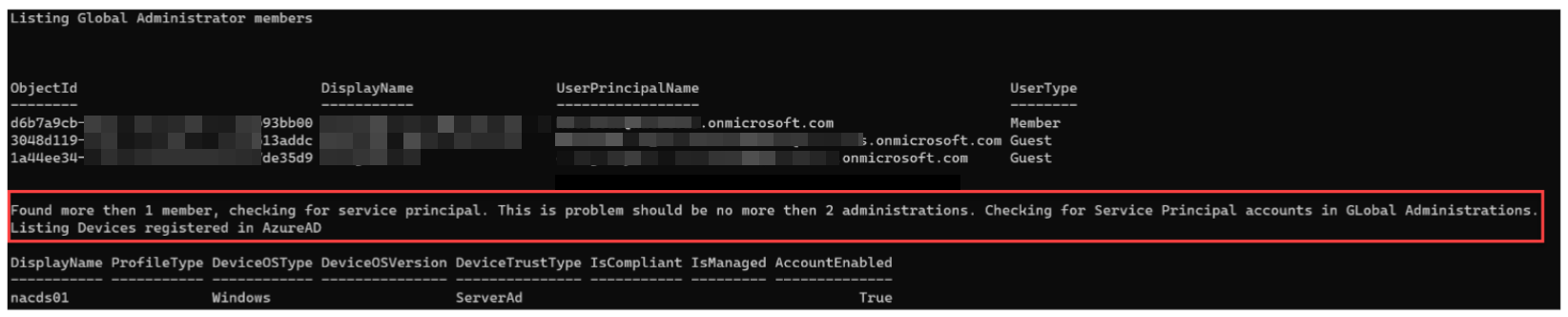
“Find-AzureADInformation.ps1” uses AzureAD PowerShell and requires a Global Administrator account due to the scans performed. The script uses the following options.
Option Description
-domainname # A domain name that will be scanned
To run the script, type the following commands.
- Open a Windows Terminal PowerShell as Administrator (Microsoft, 2022)
- Navigate to the downloaded code
- Type the following command, replacing “domain.com” with your “domain” Note: A login Windows will appear and may be hidden behind the Terminal.
.\find-AzureADInformation.ps1 -DomainName domain.com
The script outputs information to JSON files and reports issues it finds, as shown.
The scripts use PowerShell 5.1; this was chosen due to a limitation on the AzureAD PowerShell. The code will need to use Microsoft Azure Graph API to enable the code to run on the current PowerShell 7.
