Australian Banks: A Deep Dive into Cipher Security
Australian Banks: A Deep Dive into Cipher Security
Australian Banks: A Deep Dive into Cipher Security
In a world increasingly reliant on online banking, the security protocols and ciphers adopted by banks are more critical than ever. Curiosity led me to investigate which Australian banks might still be operating with outdated ciphers. My method? A PowerShell script, albeit a straightforward one, to parse outputs from SSLSCAN and collate them into comprehensible CSV files.
SSLSCAN can be downloaded here: rbsec github
# Loading target banks from a file
$scantargets = Get-Content -Path .\\internet_banks.txt
$OutputReportLocation = $OutputReportLocation
$CSVReportName = "Report.csv"
# Running sslscan for each bank
foreach ($target in $scantargets) {
$cleartarget = $target -replace '/', '_'
.\\sslscan.exe --xml=.\internetoutput\\$($cleartarget).xml $target
}
# Creating a CSV to capture protocol information
Add-Content -Path ".\\$($CSVReportName)" -Value "Hostname,SSL2,SSL3,TLS1_0,TLS1_1,TLS1_2,TLS1_3"
Get-ChildItem $OutputReportLocation -Filter *.xml | Foreach-Object {
$xmlObject = [XML](Get-Content -Path "$($OutputReportLocation)$($_.Name)")
# Capturing details of different protocols
$protocols = $xmlObject.document.ssltest.protocol
$output = "${xmlObject.document.ssltest.host},$(
($protocols | Where-Object {($_.type -eq "ssl") -and ($_.version -eq "2")}).enabled),$(
($protocols | Where-Object {($_.type -eq "ssl") -and ($_.version -eq "3")}).enabled),$(
($protocols | Where-Object {($_.type -eq "tls") -and ($_.version -eq "1.0")}).enabled),$(
($protocols | Where-Object {($_.type -eq "tls") -and ($_.version -eq "1.1")}).enabled),$(
($protocols | Where-Object {($_.type -eq "tls") -and ($_.version -eq "1.2")}).enabled),$(
($protocols | Where-Object {($_.type -eq "tls") -and ($_.version -eq "1.3")}).enabled)"
Add-Content -Path ".\\$($CSVReportName)" -Value $output
}
# Creating another CSV to capture cipher information
Add-Content -Path ".\\Ciphers_$($CSVReportName)" -Value "Hostname,Status,SSLVersion,Cipher,Strength,Bits"
Get-ChildItem $OutputReportLocation -Filter *.xml | Foreach-Object {
$xmlObject = [XML](Get-Content -Path "$($OutputReportLocation)$($_.Name)")
foreach ($ciphers in $xmlObject.document.ssltest.cipher) {
$output = "${xmlObject.document.ssltest.host},${ciphers.status},${ciphers.sslversion},${ciphers.cipher},${ciphers.strength},${ciphers.bits}"
Add-Content -Path ".\\Ciphers_$($CSVReportName)" -Value $output
}
}
Upon collating the data, I merged the CSV files into Excel for a clearer visualization, focusing on both Protocol versions and Ciphers.
Observations:
- No banks utilized SSL 2 or SSL 3.
- Alarming as it might sound, 5 banks still used TLS 1.0, pointing to a potential vulnerability.
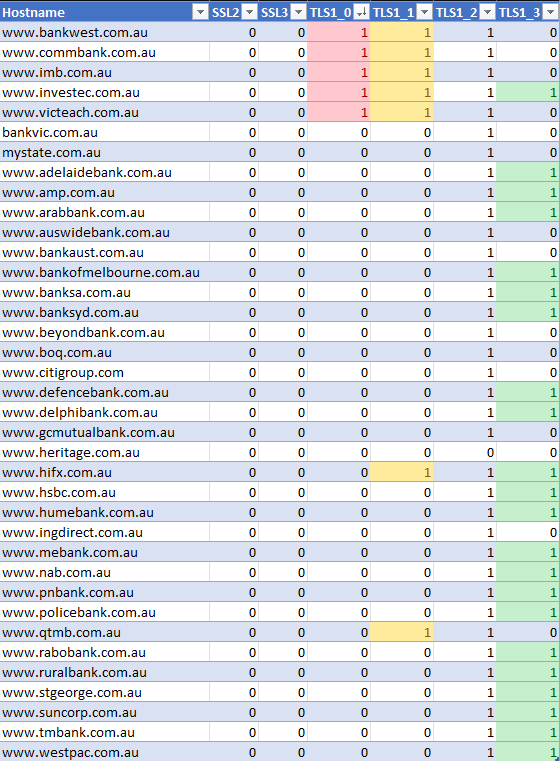
Zooming in on the ciphers, I found a significant use of weak ciphers. The plot thickens when we shift our gaze from the primary websites of banks to their Internet Banking counterparts. While the main pages might seem secure at first glance, vulnerabilities become apparent in some of the banks’ internet banking domains.
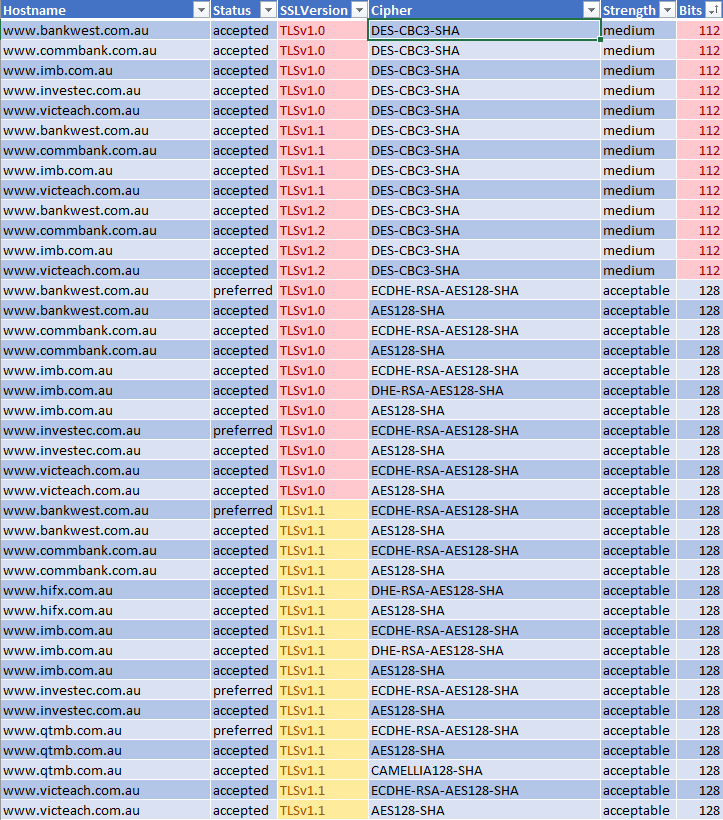
A case in point: Westpac, one of the ‘Big Four’, exhibits robust protocols on its main page but falls short in the internet banking arena.
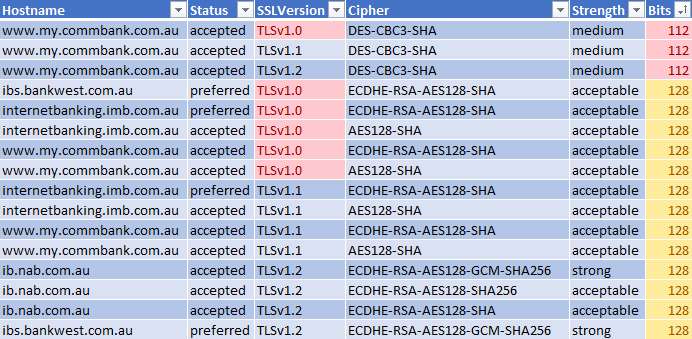
Meanwhile, some banks continue to cling to 112 bits and TLS 1.0 ciphers.

Final Verdict: From the comprehensive cipher and protocol review, CommBank and IMB stood out with notably weak protocols and ciphers. If you’re banking online, it’s essential to be aware of these vulnerabilities. So, given the results, which bank would you entrust with your transactions and savings?
