Exploring the Certificate Store via PowerShell
A Different View: Exploring the Certificate Store via PowerShell
While many turn to the certificate MMC to observe their certificates, I opted for a different angle using PowerShell. Here’s how you can harness PowerShell to extract information about your certificates:
1. To List All Trusted Root CA in the Local Machine:
$LocalMachineRootCA = (Get-ChildItem Cert:\LocalMachine\Root\) | Select-Object FriendlyName, Subject, Issuer, NotAfter, NotBefore, HasPrivateKey, Name, Thumbprint
$LocalMachineRootCA | Export-Csv -Path .\LocalMachineRootCA.csv -NoTypeInformation
2. To Identify Expired Certificates:
$LocalMachineRootCAExpired = (Get-ChildItem Cert:\LocalMachine\Root\) | Where-Object {$_.NotAfter -lt (Get-Date)} | Select-Object FriendlyName, Subject, Issuer, NotAfter, NotBefore, HasPrivateKey, Name, Thumbprint
$LocalMachineRootCAExpired | Export-Csv -Path .\LocalMachineRootCAExpired.csv -NoTypeInformation
3. To Find Certificates Expired Across Stores:
$AllExpiredCertificates = Get-ChildItem cert:\ -Recurse | Where-Object {$_ -is [System.Security.Cryptography.X509Certificates.X509Certificate2] -and $_.NotAfter -lt (Get-Date)} | Select-Object -Property Name, FriendlyName, NotAfter, HasPrivateKey, Subject, Thumbprint, Location
$AllExpiredCertificates | Export-Csv -Path .\AllExpiredCertificates.csv -NoTypeInformation
Complete code:
#List all Trusted Root CA in Local Machine
$LocalMachineRootCA = (Get-ChildItem Cert:\LocalMachine\Root\) | Select-Object FriendlyName, Subject, Issuer, NotAfter, NotBefore, HasPrivateKey, Name, Thumbprint
# Export results to CSV
$LocalMachineRootCA | Export-Csv -Path .\LocalMachineRootCA.csv -NoTypeInformation
# Expired Certificates
$LocalMachineRootCAExpired = (Get-ChildItem Cert:\LocalMachine\Root\) |Where-Object {$_.NotAfter -lt (Get-Date)} | Select-Object FriendlyName, Subject, Issuer, NotAfter, NotBefore, HasPrivateKey, Name, Thumbprint
$LocalMachineRootCAExpired | Export-Csv -Path .\LocalMachineRootCAExpired.csv -NoTypeInformation
# Looking for certificates expired across stores.
$AllExpiredCertificates = Get-ChildItem cert:\ -Recurse | Where-Object {$_ -is [System.Security.Cryptography.X509Certificates.X509Certificate2] -and $_.NotAfter -lt (Get-Date)} | Select-Object -Property Name,FriendlyName,NotAfter, HasPrivateKey, Subject, Thumbprint, Location
$AllExpiredCertificates | Export-Csv -Path .\AllExpiredCertificates.csv -NoTypeInformation
Upon inspecting the results, I observed several expired certificates in my system, with a few notable ones in my Root Store.
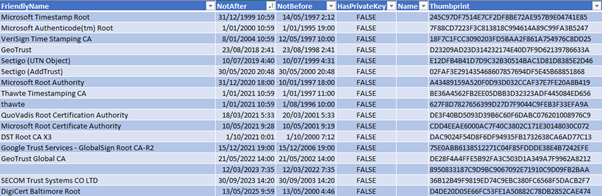
While expired certificates can introduce errors and even allow some software to persistently run, it’s possible to disable checks against the store. However, it’s advisable to periodically review these certificates and remove any that aren’t necessary.
As I delved deeper, I explored the realm of private keys, specifically seeking certificates capable of encrypting information via a private key. I discovered that my workstation’s certificate did possess a private key, which was anticipated.
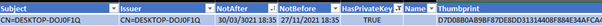
Should we discard expired certificates? Surprisingly, no. Instead, certificates ought to be revoked. Even though an expired certificate should not be utilized, it was validated during its active period. Software or applications crafted during that time might still depend on it. For a more comprehensive understanding, consider these resources:
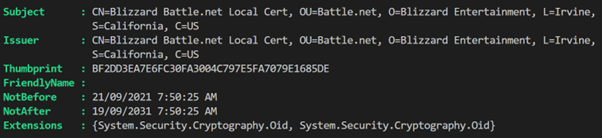
One certificate, in particular, piqued my interest: one from Blizzard Entertainment. Spanning a life of 10 years, I speculate Blizzard employs this certificate for internal communication within their gaming services. It’s intriguing to observe firms pivoting to their own CA. While I trust this CA – as it was installed alongside one of their tools – it’s intriguing that I don’t possess the corresponding private key. Also, the certificate seems to be localized to my workstation.
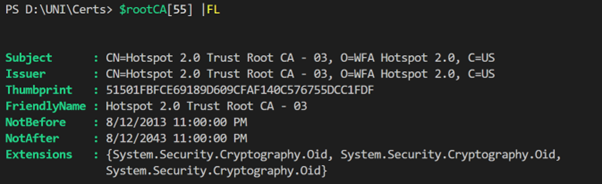
On the flip side, a certificate I’m wary of is “Hotspot 2.0 Trust Root CA – 03.” With a staggering 30-year lifespan, it seems a tad excessive. I’ll need to conduct further research before deciding its fate.